
Tryhackme Sighunt Writeup/Walkthrough
This room aims to be a supplementary room for Sigma rule creation. In this scenario, you will act as one of the Detection Engineers that will craft Sigma Rules based on the Indicators of Compromise (IOCs) collected by your Incident Responders.

Room Link : https://tryhackme.com/room/sighunt
Prerequisites
This room requires basic knowledge of detection engineering and Sigma rule creation. I recommend going through the following rooms before attempting this challenge.

SigHunt Interface
Before we proceed, let’s deploy the attached machine in this task since it may take up to 3–5 minutes to initialize the services.
We will use this link to access the interface — http://MACHINE_IP
How to use the SigHunt Interface:
- Run — Submit your Sigma rule and see if it detects the malicious IOC.
- Text Editor — Write your Sigma rule in this section.
- Create Rule — Create a Sigma rule for the malicious IOC.
- View Log — View the log details associated with the malicious IOC.

Huntme Incident
Scenario
You are hired as a Detection Engineer for your organization. During your first week, a ransomware incident has just concluded, and the Incident Responders of your organization have successfully mitigated the threat. With their collective effort, the Incident Response (IR) Team provided the IOCs based on their investigation. Your task is to create Sigma rules to improve the detection capabilities of your organization and prevent future incidents similar to this.
Indicators of Compromise
Based on the given incident report, the Incident Responders discovered the following attack chain:
- Execution of malicious HTA payload from a phishing link.
- Execution of Certutil tool to download Netcat binary.
- Netcat execution to establish a reverse shell.
- Enumeration of privilege escalation vectors through PowerUp.ps1.
- Abused service modification privileges to achieve System privileges.
- Collected sensitive data by archiving via 7-zip.
- Exfiltrated sensitive data through cURL binary.
- Executed ransomware with huntme as the file extension.
In addition, the Incident Responders provided a table of IOCs at your disposal.

Rule Creation Standards
The Detection Engineering Team follows a standard when creating a Sigma Rule. You may refer to the guidelines below.

Answer the questions below :
What is the Challenge #1 flag?
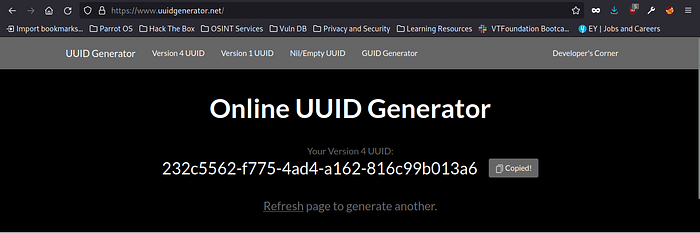
First of all go the Online UUID generator and copy that code and paste it in the id section of suspicious_mshta_execution.yml
❯ code -->
title: sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: HTA payload detection
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
ParentImage|endswith: '\chrome.exe'
Image|endswith: '\mshta.exe'
condition: selection
After writing the sigma rule we can run the code $suspicious_mshta_execution.yml to get the flag.

What is the Challenge #2 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: certutil download
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\certutil.exe'
CommandLine|contains:
- ' -urlcache '
- ' -split '
- ' -f '
condition: selection
After writing the sigma rule we can run the code $certutil_file_ingress.yml to get the flag.
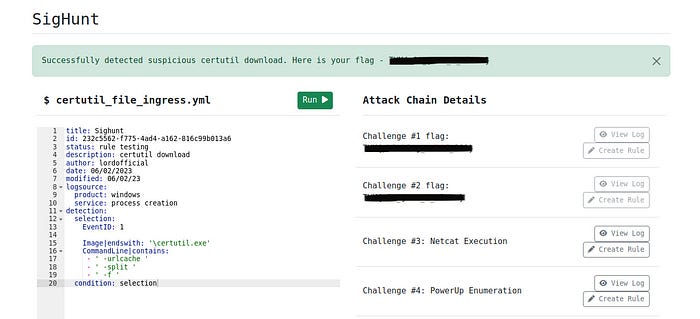
What is the Challenge #3 flag?
❯ code -->
title: sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: Netcat Execution
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection1:
EventID: 1
Image|endswith: '\nc.exe'
CommandLine|contains|all:
- ' -e '
selection2:
Hashes|contains: '523613A7B9DFA398CBD5EBD2DD0F4F38'
condition: selection1 or selection2
After writing the sigma rule we can run the code $netcat_reverse_shell.yml to get the flag.

What is the Challenge #4 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: PowerUp Enumeration
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\powershell.exe'
CommandLine|contains:
- 'Invoke-AllChecks'
- 'PowerUp'
condition: selection
After writing the sigma rule we can run the code $powerup_enumeration.yml to get the flag.
What is the Challenge #5 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: Service Binary
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\sc.exe'
CommandLine|contains|all:
- ' config '
- ' binPath= '
- ' -e '
condition: selection
After writing the sigma rule we can run the code $service_binary_privesc.yml to get the flag.
What is the Challenge #6 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: RunOnce Persistence
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\reg.exe'
CommandLine|contains:
- ' add '
- ' RunOnce '
condition: selection
After writing the sigma rule we can run the code $runonce_persistence.yml to get the flag.
What is the Challenge #7 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: 7z Archive
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\7z.exe'
CommandLine|contains:
- ' a '
- ' -p '
condition: selection
After writing the sigma rule we can run the code $7z_suspicious_archive.yml to get the flag.
What is the Challenge #8 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: Curl Data
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 1
Image|endswith: '\curl.exe'
CommandLine|contains:
- ' -d '
condition: selection
After writing the sigma rule we can run the code $ curl_exfiltration.yml to get the flag.
What is the Challenge #9 flag?
❯ code -->
title: Sighunt
id: 232c5562-f775-4ad4-a162-816c99b013a6
status: rule testing
description: Ransomware File
author: lordofficial
date: 06/02/2023
modified: 06/02/23
logsource:
product: windows
service: process_creation
detection:
selection:
EventID: 11
TargetFilename: '*.huntme'
condition: selection
After writing the sigma rule we can run the code $ransomware_file_encryption.yml to get the flag.
